Beware of Phishing Trap
Before replying to any email, you must confirm the identity of the sender, especially if the email involves sensitive content such as money, personal information or account password, etc. please pay special attention. Usually, a phishing email will contain one or more characteristics as below:
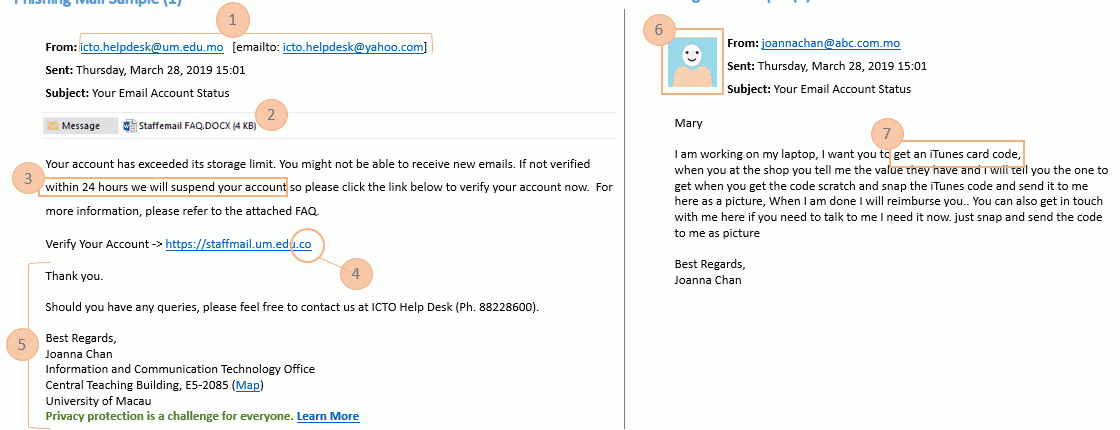
1. Be aware of the non-official email address domain. For example, a notice from ICTO Help Desk is unlikely to come from the following email addresses. Please note that if an email address is shown with a display name, it may not be used to verify of the sender’s identity. For this case, you need to verify the sender’s email address in “< >” or “[ ]”;
- @ — For official email, it is unlikely to come from third party email service;
- @ — @connect.um.edu.mo is used in the student and alumni service but not an official staff email address.
2. Beware of attachments — Email attachment is the most common platform for malicious software. When you get a message with an attachment, DO NOT open it unless you are expecting it and absolutely certain that it is legitimate;
3. Urge to do something is one of the typical phishing characteristics, an urgent call to action makes you more likely to cooperate, e.g. urge to perform account verification, purchase some prepaid cards, money transfer, etc. If a message states that you must act immediately or you will lose access, so you must calmly deal with it. Cybercriminals often use intimidation and hope you will follow the action without thinking;
4. Incorrect URL link — It will take the recipient to a fraudulent website instead of the genuine links;
5. Fake email signature — Hackers may obtain the email signature from somewhere. Even if it looks real, you are not recommended to identify the authenticity of email with the email signature. However, if the sender’s email signature is unusual, you need to pay special attention;
6. Do not trust the sender’s photo — Hackers may obtain someone’s photo from somewhere, e.g. social media website;
7. Using different communication channels — For any suspicious requests, you can use different communication channels to determine the authenticity of the email sender. For example, instant messaging apps, or voice call, etc.
Reference
- Office for Personal Data Protection, Macao
- Personal Data Protection Act, Macao
- Privacy Policy, UM
- Guidelines for Handling Confidential Information, UM
- Acceptable Use Policy on ICTO Computing Facilities Campus Network and Internet
- Guidelines for Mass Email and E-mail Groups
- How can I identify a phishing, fake email and websites?
- What you need to know about EU General Data Protection Regulation?
- Data Privacy in an Era of Compliance
- Beware of suspicious emails with intimidating contents!
- Other Information Security Tips