Information Security Tips (January 2024) – Do not let yourself to be the next victim of phishing scams
To: All Users
Online services have become an indispensable part in our daily life, thus making Internet scams more prevalent and widespread, covering a wide range of areas such as shopping, job hunting, investing, charity, lottery, etc. There is a Cantonese saying, “An old trick is fine, as long as it works” implying that many traditional scams are repackaged in new forms and carried out on the Internet or over the phone. The tactics are constantly changing, making it hard for people to protect.
However, all scams have a common goal, whether they are tricking users to give their account numbers, passwords or personal information, the ultimate goal is money. As long as you raise your security awareness and always “fact‑check”, you can reduce the risk of being scammed. Remember the three key principles to prevent fraud:
- Stay calm and don’t be flustered: Fraudsters often use threatening words over phone, text messages or emails to cause victims to lose their composure and fall into their trap, especially if they claim themselves to be law enforcement, government or bank officials. Just stop and think! Try to buy time to verify the truth of the matter or consult with family and friends.
- Don’t be greedy: Never let the mentality of “Fear of missing out” to blind your judgment. There’s no free lunch in the world. If there’s any promotional sale or investment opportunity, make sure to understand it clearly and verify its authenticity to avoid losing more than you gain.
- Never casually disclose personal information: Personal information is equivalent to money. You should not reveal your personal information casually, as it is not just your data that can ultimately be stolen, but your personal identity, which can then be used to defraud money or engage in illegal activities.
Pay more attention to anti-fraud information and naturally raise your anti-fraud awareness, so that you won’t give fraudsters an opportunity to take advantage. The following are some examples of scam messages:
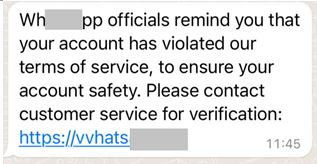
Pretending to be an instant messaging software notification, with disturbing words. But one thing to note is that the “w” letter in URL is actually impersonated by two “v” letters.

Suspicious text messages from strangers. Scammers may use social engineering scams to carry out all kinds of fraud, they will use the tactic of “played the long game” and communicate with the victim for a long time to win their favor, which means to defraud a large amount of money.
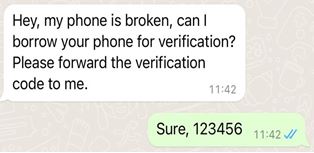
Compromising verification codes is a common method of hijacking other people’s accounts, including communication software, bank transfers, etc. Verification codes are used for personal identity verification or account operation verification, which is a matter of personal privacy, and should not be disclosed. Actually, using someone else’s phone number for verification is completely unreasonable, and the sender’s account may have been compromised.



