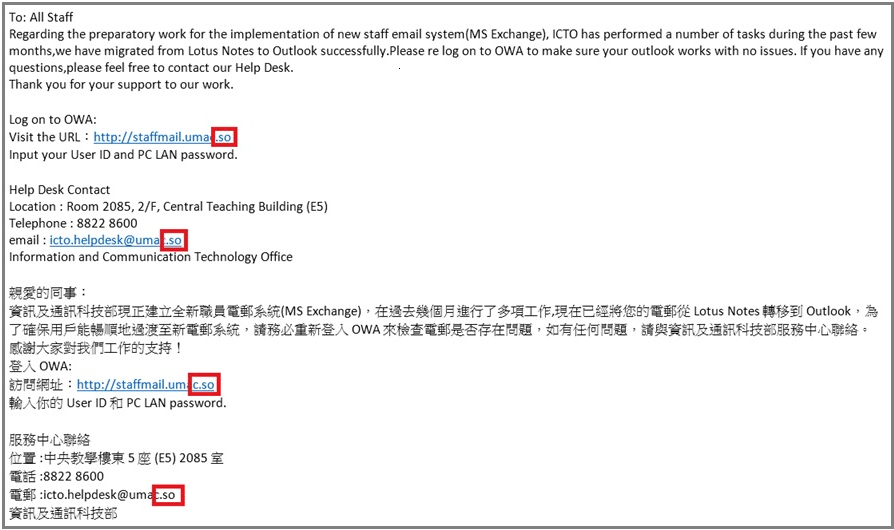
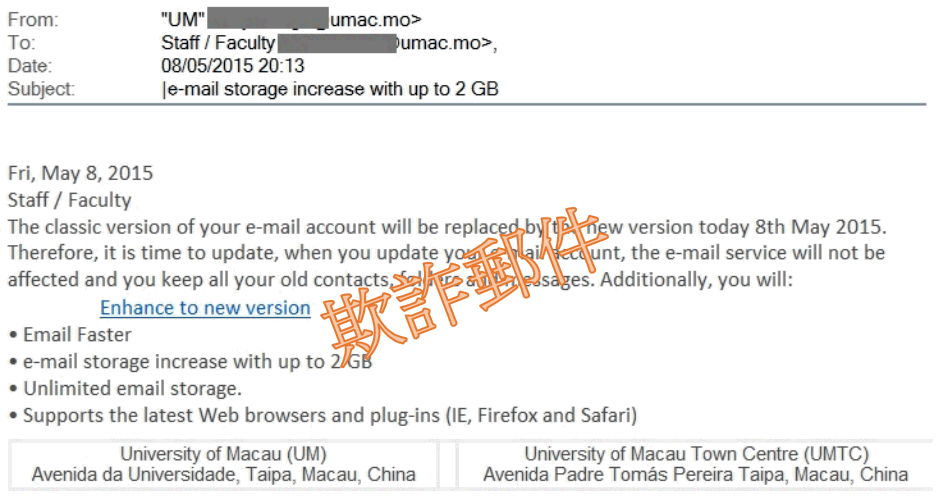
To All Users,
Please be informed that a high security vulnerability in UNIX Bash shell (Shellshock, also known as Bashdoor) was
disclosed on 24 Sept. 2014, which would eventually let remote attackers bypass system authentication and execute
arbitrary commands.
Affected systems:
– CentOS
– Mac OS
– Redhat Enterprise Linux
– Ubuntu
– And any systems which utilize BASH as the default system shell
System administrators and users of UNIX / Linux / Mac are advised to update the BASH of their system to the latest available version.
For CentOS, Redhat Enterprise Linux users, detailed update information can be found:
https://access.redhat.com/articles/1200223
Mac OS
For Mavericks 10.9.5 – http://support.apple.com/kb/DL1769
For Mountain Lion – http://support.apple.com/kb/DL1768
For Lion – http://support.apple.com/kb/DL1767
Ubuntu
http://www.ubuntu.com/usn/usn-2363-1/
http://www.ubuntu.com/usn/usn-2364-1/
More general information can be found here
CVE-2014-6271 – http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
CVE-2014-6277 – http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6277
CVE-2014-7169 – http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7169
CVE-2014-7186 – http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7186
CVE-2014-7187 – http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7187
Thank you for your attention. For further inquiries, please feel free to contact our Help Desk (Ext. 8600, Email: @).
Information and Communication Technology Office