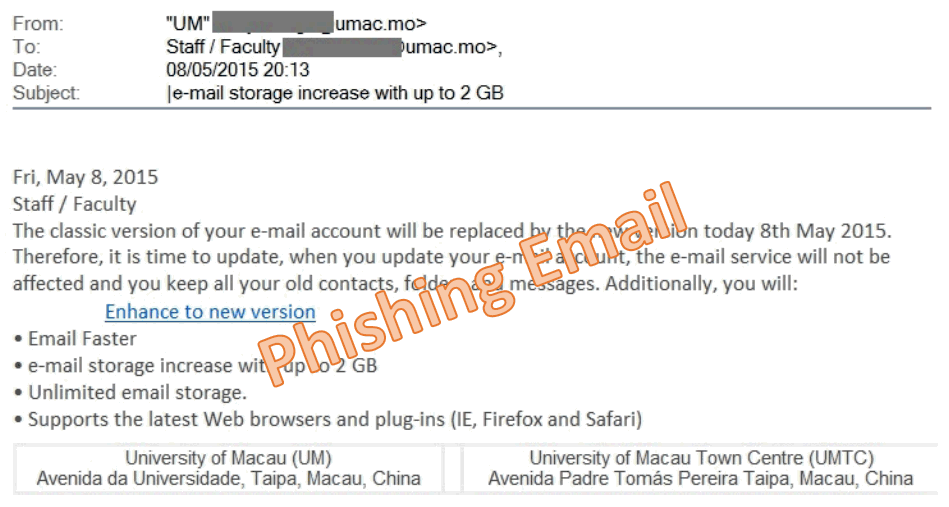
Users are advised to uninstall QuickTime for Windows immediately
Two critical security vulnerabilities affecting QuickTime for Windows were discovered
Due to the discovery of two critical security vulnerabilities that would not be patched, users of QuickTime player for Windows are advised to uninstall the program as soon as possible.
Apple has ended the support for QuickTime for Windows and will not provide patches for the security vulnerabilities for the said software on the Windows platform. As such, users are strongly recommended to uninstall QuickTime to protect personal computers from possible exploits.
Please note that this does not apply to QuickTime on Mac OSX.
Here are the steps to uninstall QuickTime from your Windows computer:
For Windows 7:
- Press the “Start button”.
- Select “Control Panel”.
- Choose “Programs and features”.
- Find QuickTime in the list of programs, and select “Uninstall”.
For more information about the security vulnerabilities associated with QuickTime, please visit the following link: http://zerodayinitiative.com/advisories/ZDI-16-241/
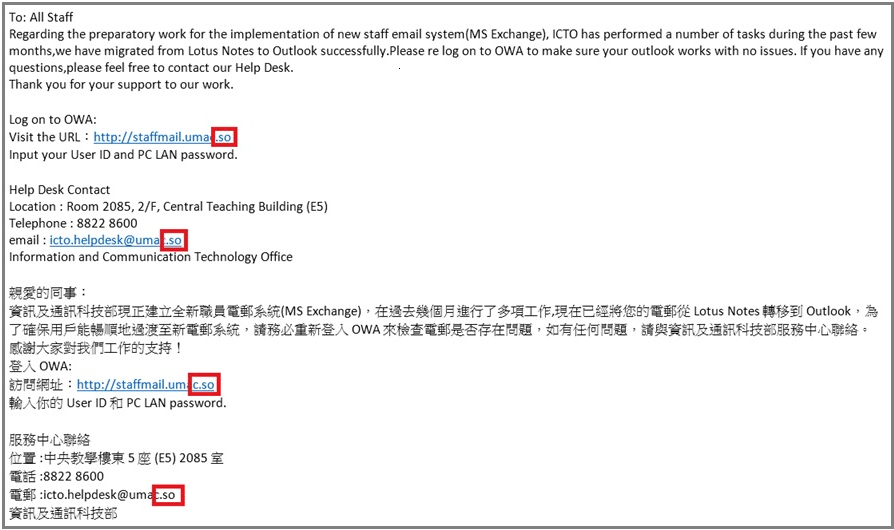
If you have any further queries, please feel free to contact our Help Desk.
Help Desk
Location : Room 2085, 2/F, Central Teaching Building (E5), eMap
Telephone : 8822 8600
Email : @
Information and Communication Technology Office