Information Security Tips (March 2022) – How to download and install software in a secure manner?
The daily online activities may bring risk to your electronic device, because most threats that infect your computer system, such as viruses and malware, usually come from the programs that you download and install from the Internet.
Here are the 4 tips to download and install software in a relatively safe way:
1. Only download software from the official website of the vendor/publisher
You are always recommended to download the software only from the official website of the vendor or publisher, and avoid to download software installers from third party websites. It is because some of the installers have been embedded with various types of ads, which may install additional malicious programs to your system.
2. Always delete any software that is downloaded to your device automatically
This often happens when you accidentally visit malicious websites on the Internet and the websites will send their malicious programs directly to your device. When this happens, always delete the application that is downloaded automatically to your device without your acknowledgement.
3. Don’t download any type of cracked or hacked programs
A program that includes any type of crack or hack is certainly a malicious program. When you run it, it will install malicious codes into your system or device. It tends to disturb your system and send malicious commands to it. It is better for you to stay away from cracked or hacked software.
4. Follow the installation steps carefully
When you download a software installer even from the official website, do not just mindlessly click “next”. You have to follow the installation steps very carefully because a bad software vendor might embed malware or adware into their installer. Make sure to tick off any unnecessary options during the installation.
Reference
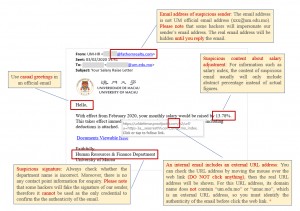
· Don’t Let a Phishing Scam Reel You In
· How can I identify a phishing, fake email and websites?
· Beware of Phishing Trap
· Other Information Security Tips