Information Security is everyone’s responsibility
Did you know? In the recent years, there were different types of industry occurred data breach in the world, involving education institutions, airline companies, government departments, banking and financial institutions, e-commerce corporations, web service providers, etc. More than half of the breaches were caused by activities directly attributable to human errors, including lost devices, physical loss and unintended disclosure. These breaches were arguably preventable through basic information security protection safeguards.
- What can you do everyday to protect data? No matter what types of industry you are working in, you may need to transmit, process, access, and share such varying data elements. There is not a “one size fits all” blueprint for information security controls that all industries can follow. Yet all members have a responsibility to know basic information security protections to safeguard data and prevent those data from being mishandled.
- Understand where, how, and to whom you are sending data: Many breaches occur because of our careless where we accidentally post confidential information publicly, mishandle or send confidential information to the wrong party. Taking care to know how you are transmitting or posting data is critical.
- Create complex and unique passwords: Use different passwords for different accounts, in particular those for handling confidential data.
Enable two-factor authentication: Two-factor authentication can prevent unauthorized access even if your login credentials are stolen or lost. - Protect your devices: Besides using password lock, it is also recommended to use some biometric technologies to protect your smartphone and tablet. It is critical to keep curious minds from accessing personal information, work email, or retail/banking applications. It also helps to protect your device in case you lost or misplaced it.
- Update your computing devices: Ensure the operating system, web browser, and applications on all your electronic devices are updated to the latest version.
- Getting ready to send data to a vendor or sign a contract? In daily work, we are obligated to ensure that the University’s confidential information are properly protected, especially if we need to use an outsource service or a cloud service. If the service involves confidential information, you must consider the related information security technology before the project begins or signing the contract, which ensures the data is protected properly.
Reference
- Office for Personal Data Protection, Macao
- Personal Data Protection Act, Macao
- Privacy Policy, UM
- Guidelines for Handling Confidential Information, UM
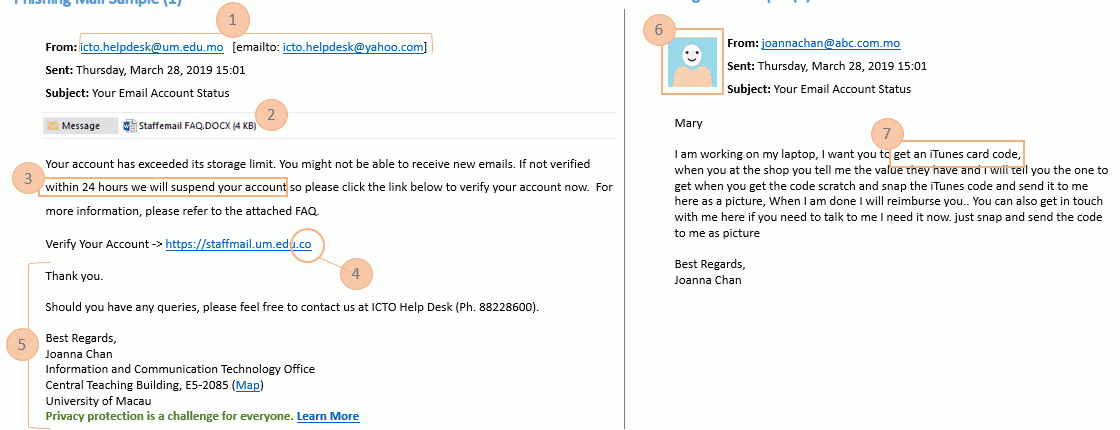
- How can I identify a phishing, fake email and websites?
- What you need to know about EU General Data Protection Regulation?
- Other Information Security Tips